Have you ever wondered how vulnerable your business is to cyberattacks? According to recent reports, nearly 43% of cyberattacks target small businesses, often exploiting weak security measures.
One of the most overlooked yet highly effective ways to protect your company is through Multi-Factor Authentication (MFA). This extra layer of security makes it significantly harder for hackers to gain access, even if they have your password.
This article explains how to implement Multi-Factor Authentication for your small business. With this knowledge, you’ll be able to take a crucial step in safeguarding your data and ensuring stronger protection against potential cyber threats.
Why is Multi-Factor Authentication Crucial for Small Businesses?
Before diving into the implementation process, let’s take a step back and understand why Multi-Factor Authentication (MFA) is so essential. Small businesses, despite their size, are not immune to cyberattacks. In fact, they’re increasingly becoming a target for hackers. The reality is that a single compromised password can lead to massive breaches, data theft, and severe financial consequences.
This is where MFA comes in. MFA is a security method that requires more than just a password to access an account or system. It adds additional layers, typically in the form of a time-based code, biometric scan, or even a physical security token. This makes it much harder for unauthorized individuals to gain access to your systems, even if they’ve obtained your password.
It’s no longer a matter of if your small business will face a cyberattack, but when. Implementing MFA can significantly reduce the likelihood of falling victim to common online threats, like phishing and credential stuffing.
What is Multi-Factor Authentication?
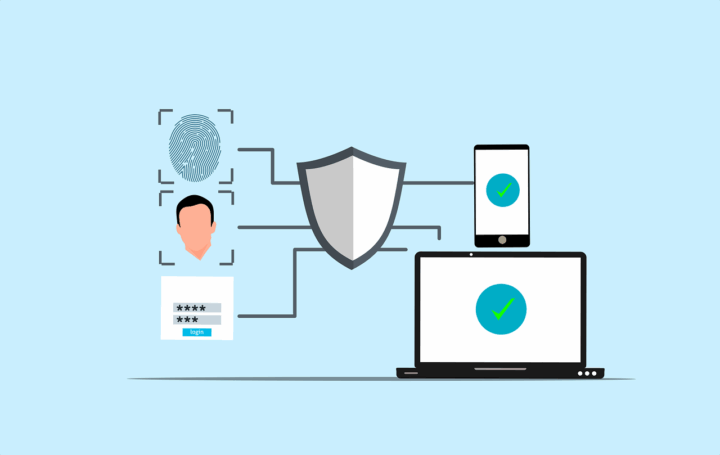
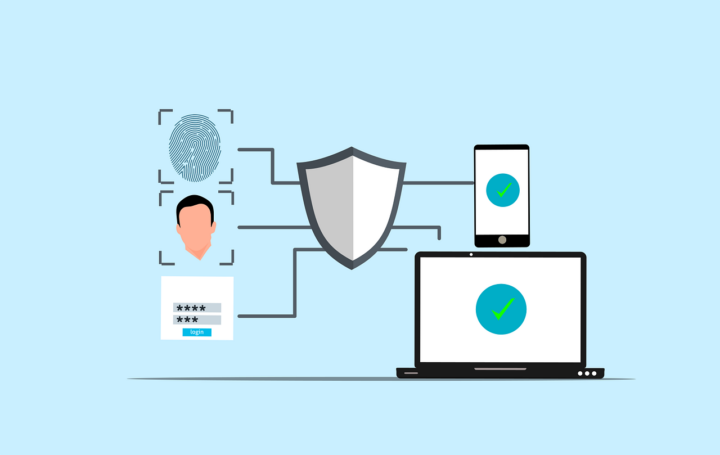
Multi Factor Authentication (MFA) is a security process that requires users to provide two or more distinct factors when logging into an account or system. This layered approach makes it more difficult for cybercriminals to successfully gain unauthorized access. Instead of relying on just one factor, such as a password, MFA requires multiple types of evidence to prove your identity. This makes it a much more secure option.
To better understand how MFA works, let’s break it down into its three core components:
Something You Know
The first factor in MFA is the most traditional and commonly used form of authentication (knowledge-based authentication). It usually involves something only the user is supposed to know, like a password or PIN. This is the first line of defense and is often considered the weakest part of security. While passwords can be strong, they’re also vulnerable to attacks such as brute force, phishing, or social engineering.
Example: Your account password or a PIN number
While it’s convenient, this factor alone is not enough to ensure security, because passwords can be easily stolen, guessed, or hacked.
Something You Have
The second factor in MFA is possession-based. This involves something physical that the user must have access to in order to authenticate. The idea is that even if someone knows your password, they wouldn’t have access to this second factor. This factor is typically something that changes over time or is something you physically carry.
Examples:
- A mobile phone that can receive SMS-based verification codes (also known as one-time passcodes).
- A security token or a smart card that generates unique codes every few seconds.
- An authentication app like Google Authenticator or Microsoft Authenticator, which generates time-based codes that change every 30 seconds.
These items are in your possession, which makes it far more difficult for an attacker to access them unless they physically steal the device or break into your system.
Something You Are
The third factor is biometric authentication, which relies on your physical characteristics or behaviors. Biometric factors are incredibly unique to each individual, making them extremely difficult to replicate or fake. This is known as inherence-based authentication.
Examples:
- Fingerprint recognition (common in smartphones and laptops).
- Facial recognition (used in programs like Apple’s Face ID).
- Voice recognition (often used in phone systems or virtual assistants like Siri or Alexa).
- Retina or iris scanning (used in high-security systems).
This factor ensures that the person attempting to access the system is, indeed, the person they claim to be. Even if an attacker has your password and access to your device, they would still need to replicate or fake your unique biometric traits, which is extraordinarily difficult.
How to Implement Multi-Factor Authentication in Your Business
Implementing Multi-Factor Authentication (MFA) is an important step toward enhancing your business’s security. While it may seem like a complex process, it’s actually more manageable than it appears, especially when broken down into clear steps. Below is a simple guide to help you get started with MFA implementation in your business:
Assess Your Current Security Infrastructure
Before you start implementing MFA, it’s crucial to understand your current security posture. Conduct a thorough review of your existing security systems and identify which accounts, applications, and systems need MFA the most. Prioritize the most sensitive areas of your business, including:
- Email accounts (where sensitive communications and passwords are often sent)
- Cloud services (e.g., Google Workspace, Microsoft 365, etc.)
- Banking and financial accounts (vulnerable to fraud and theft)
- Customer databases (to protect customer data)
- Remote desktop systems (ensuring secure access for remote workers)
By starting with your most critical systems, you ensure that you address the highest risks first and establish a strong foundation for future security.
Choose the Right MFA Solution
There are many MFA solutions available, each with its own features, advantages, and pricing. Choosing the right one for your business depends on your size, needs, and budget. Here are some popular options that can cater to small businesses:
Google Authenticator
A free, easy-to-use app that generates time-based codes. It offers an effective MFA solution for most small businesses.
Duo Security
Known for its user-friendly interface, Duo offers both cloud-based and on-premises solutions with flexible MFA options.
Okta
Great for larger businesses but also supports simpler MFA features for small companies, with a variety of authentication methods like push notifications and biometric verification.
Authy
A solution that allows cloud backups and multi-device syncing. This makes it easier for employees to access MFA codes across multiple devices.
When selecting an MFA provider, consider factors like ease of use, cost-effectiveness, and scalability as your business grows. You want a solution that balances strong security with practicality for both your organization and employees.
Implement MFA Across All Critical Systems
Once you’ve chosen an MFA provider, it’s time to implement it across your business. Here are the steps to take:
Step 1: Set Up MFA for Your Core Applications
Prioritize applications that store or access sensitive information, such as email platforms, file storage (Google Drive, OneDrive), and customer relationship management (CRM) systems.
Step 2. Enable MFA for Your Team
Make MFA mandatory for all employees, ensuring it’s used across all accounts. For remote workers, make sure they are also utilizing secure access methods like VPNs with MFA for extra protection.
Step 3. Provide Training and Support
Not all employees may be familiar with MFA. Ensure you offer clear instructions and training on how to set it up and use it. Provide easy-to-access support resources for any issues or questions they may encounter, especially for those who might not be as tech-savvy.
Remember, a smooth implementation requires clear communication and proper onboarding, so everyone understands the importance of MFA and how it protects the business.
Regularly Monitor and Update Your MFA Settings
Cybersecurity is a continuous process, not a one-time task. Regularly reviewing your MFA settings is crucial to ensuring your protection remains strong. You should:
Keep MFA Methods Updated
Consider adopting stronger verification methods, such as biometric scans, or moving to more secure authentication technologies as they become available.
Re-evaluate Authentication Needs
Regularly assess which users, accounts, and systems require MFA, as business priorities and risks evolve.
Respond to Changes Quickly
If employees lose their security devices (e.g., phones or tokens), make sure they can quickly update or reset their MFA settings. Also, remind employees to update their MFA settings if they change their phone number or lose access to an authentication device.
Test Your MFA System Regularly
After implementation, it’s essential to test your MFA system regularly to ensure it’s functioning properly. Periodic testing allows you to spot any vulnerabilities, resolve potential issues, and ensure all employees are following best practices. This could include simulated phishing exercises to see if employees are successfully using MFA to prevent unauthorized access.
In addition, monitoring the user experience is important. If MFA is cumbersome or inconvenient for employees, they may look for ways to bypass it. Balancing security with usability is key, and regular testing can help maintain this balance.
Common MFA Implementation Challenges and How to Overcome Them
While MFA offers significant security benefits, the implementation process can come with its own set of challenges. Here are some of the most common hurdles small businesses face when implementing MFA, along with tips on how to overcome them:
Employee Resistance to Change
Some employees may resist MFA due to the perceived inconvenience of having to enter multiple forms of verification. To overcome this, emphasize the importance of MFA in protecting the business from cyber threats. Offering training and support to guide employees through the setup process can help alleviate concerns.
Integration with Existing Systems
Not all applications and systems are MFA-ready, which can make integration tricky. It’s important to choose an MFA solution that integrates well with your existing software stack. Many MFA providers offer pre-built integrations for popular business tools, or they provide support for custom configurations if needed.
Cost Considerations
The cost of implementing MFA, especially for small businesses with tight budgets, can be a concern. Start with free or low-cost solutions like Google Authenticator or Duo Security’s basic plan. As your business grows, you can explore more robust, scalable solutions.
Device Management
Ensuring that employees have access to the necessary devices (e.g., phones or security tokens) for MFA can be a logistical challenge. Consider using cloud-based authentication apps (like Authy) that sync across multiple devices. This makes it easier for employees to stay connected without relying on a single device.
Managing Lost or Stolen Devices
When employees lose their MFA devices or they’re stolen, it can cause access issues and security risks. To address this, establish a device management policy for quickly deactivating or resetting MFA. Consider solutions that allow users to recover or reset access remotely. Providing backup codes or alternative authentication methods can help ensure seamless access recovery without compromising security during such incidents.
Now is the Time to Implement MFA
Multi-Factor Authentication is one of the most effective steps you can take to protect your business from cyber threats. By adding that extra layer of security, you significantly reduce the risk of unauthorized access, data breaches, and financial losses.
Start by assessing your current systems, selecting the right MFA solution, and implementing it across your critical applications. Don’t forget to educate your team and regularly update your security settings to stay ahead of evolving cyber threats.
If you’re ready to take your business’s security to the next level, or if you need help implementing MFA, feel free to contact us. We’re here to help you secure your business and protect what matters most.
—
This Article has been Republished with Permission from The Technology Press.